Introduction to Smart Contract Security Auditing
Hey👋
Here I am again with another article about blockchain security.
The Ethereum blockchain brought the concept of smart contracts, in which the programmer can interact with data stored on the blockchain through programmable scripts. The security of these smart contracts is very important, as these smart contracts handle important data, such as digital assets, tokens, etc.
In this article, I'll give you an introduction to smart contract security auditing. You'll learn about security best practices for smart contracts and how to audit these contracts. If you don't know what blockchain, smart contracts, and other things are, just read this article: Introduction to Blockchain Security
What is a smart contract security audit?
A smart contract security audit is a process that helps find vulnerabilities within a smart contract by examining it in depth. Usually, audits follow a four-step process:
- Smart contracts are provided to the audit team for initial analysis.
- Audit teams review the code and present their findings to the project.
- The project team makes changes based on issues found by auditors.
- The audit team releases its final report.
8 phases of the audit process (how to audit a smart contract)
Now I'll address this topic from the auditors' perspective, understand the phases of smart contract security auditing, and learn how a researcher can audit a smart contract.
1. Read specifications and documentation
First, you should read the specifications and documents to understand how the contract or project should work, as this way you'll know if you've found a considerable vulnerability.
2. Run manual tests
Interact with the contract as a normal user, trying to understand in depth how the contract works and its possibilities. This is normally done using testnets, such as Goerli, Kovan, Rinkeby, etc.
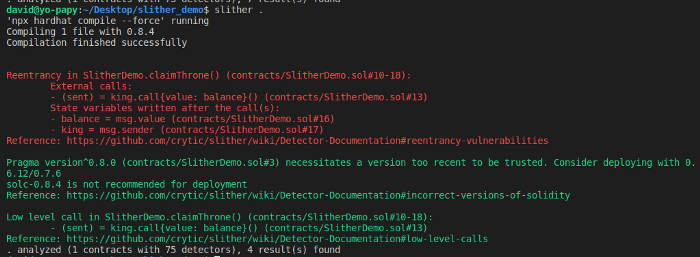
3. Run quick verification tools
Use some tools to do a quick scan of the smart contract, checking for common vulnerabilities and verifying if the smart contract is following development best practices. For this, you can use tools like Slither.
4. Manual analysis
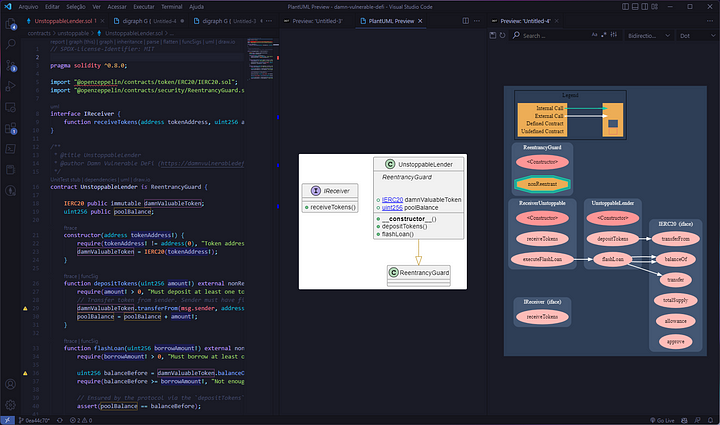
In this phase, you should analyze a smart contract in depth to find vulnerabilities using support tools like Surya and Solidity Visual Developer, which provide better visualization of the smart contract, identifying and presenting graphically and visually the relationships, internal and external calls, variables, etc.
5. Run slow verification tools
Slower tools are those that analyze the contract as deeply as possible, being able to analyze EVM bytecode, binaries, contract fuzzing, generate inputs, and thus automatically test various things in the contract. Get to know some tools:
- Echidna: It's a fuzzer, uses property tests to generate malicious inputs that break smart contracts.
- Manticore: Symbolic execution tool for analyzing smart contracts and binaries.
- Mythril: The Swiss army knife for smart contract security.
- MythX: A professional-grade cloud service that uses symbolic analysis and input fuzzing to identify common security bugs and verify smart contract code fixes.
6. Discuss and repeat steps as needed
Discuss the vulnerabilities found with the audit team and redo the necessary steps to confirm the existence of vulnerabilities, if necessary.
7. Write a Proof of Concept
Write a proof of concept for each vulnerability. This makes it easier for the project team to reproduce and verify each vulnerability and thus fix it. You can write proofs of concept using Foundry, which is an extremely fast, portable, and modular toolkit for Ethereum application development written in Rust. I intend to write an article about Foundry in the future.
8. Write a report
In this phase, you should write a detailed report about your findings and their impact. Here is an example of what a report should look like.
Use this repository to generate markdown reports: https://github.com/spearbit-audits/report-template
Most well-known smart contract vulnerabilities
Now that you already know how the audit process occurs, get to know some of the most well-known vulnerabilities and attacks in smart contracts:
Reentrancy
This vulnerability occurs when a contract sends ether to an unknown address. An attacker can build a contract at an external address that contains malicious code in the fallback function. When a contract sends ether to the malicious address, the malicious code is invoked, and this malicious code can repeat this ether transfer until the vulnerable contract runs out of balance.
Unsafe DELEGATECALL
As a result of the context-preserving nature of DELEGATECALL, building custom libraries free of vulnerabilities is not as easy as one might think. The code in the libraries themselves may be safe and free of vulnerabilities. However, when executed in the context of another application, new vulnerabilities can arise.
Private state variable
When you declare the state variable as private, this means that other contracts cannot access this data. But since everything on the blockchain is public, it's possible to access this data just by reading the memory slot where the variable is within the blockchain.
This was another article. Thank you for getting this far, and I would be very happy if you shared this article.